Do you need to track who/where/when for activities done against the OU’s in your AD?
With Windows 2003 those were difficult questions to answer, we could get some very basic information from Directory Services Auditing; but it was limited and you had to read through several cryptic events (id 566). With the advanced auditing settings with Windows 2008 R2 you can get some better information (you can do this same thing with Windows 2008 but it has to be done via command line and applied every time servers restart).
I don’t want to bore you with Windows 2003 auditing or the command line options for Windows 2008 Domains (if you need them, I will get you the information). So let’s just jump right to using Windows 2008 R2, because we can now apply the advanced auditing settings via Group Policy.
Now when you turn on the Advanced Audit Policy Configuration you are turning OFF the basic or standard Audit Policies. The Advanced Audit Policy Configuration allows you to control what AD will audit at a more granular level. Now for the focus of this discussion we are only going to talk about setting up auditing for activity on our Domain Controllers, the other systems in your environment will be a different discussion.
So where do we start so that we can answer our question at the top of this discussion?
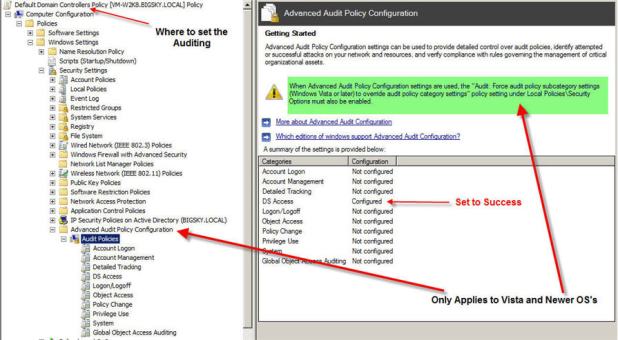
First, turn on the correct auditing. Open up Group Policy Management Editor and drill down as seen in Fig 1. **Take note of the green highlight.
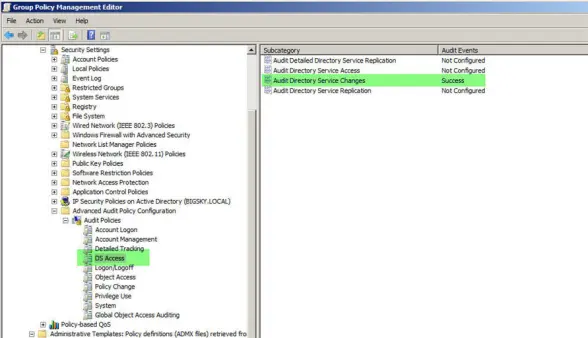
For this discussion we are focusing on DS Access and its subcategories. We only want to turn on Audit Directory Service Changes, see Fig 2. This category only generates events on domain controllers and is very useful for tracking changes to Active Directory objects that have object level auditing enabled. These events not only tell you what object and property was changed and by whom but also the new value of the affected properties.
Now that we have step 1 completed, setting up AD for auditing, it’s time to configure WHAT we want to audit. This next step is done via Active Directory Users and Computers. Open up the properties of your AD and drill down to setup the auditing for Create and Delete Organizational Unit objects as seen in Fig 3.
Fig 3
Now we need to add more granularity so we need to do this process 1 more time and this time instead of checking boxes on the Object tab we are going to check 2 boxes on the Properties tab, see Fig 4.
Fig 4
Now that our auditing is setup what type of events can we expect to see?
Here are a few examples:
In this example (Fig 5), id 5137, we see an OU being created by the Administrator.
Fig 5
Figure 6 shows a Sub OU being created.
Fig 6
Figure 7 shows id 5139, an OU being moved.
Fig 7
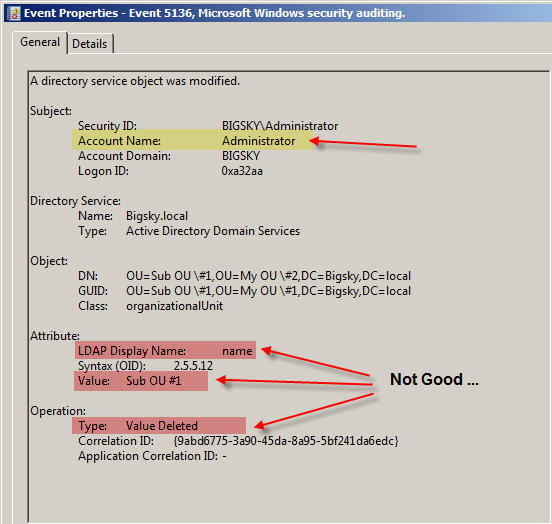
Now for the best one, this one comes as a pair of messages – OU rename, part of id 5136.
Figure 8 shows the first part of the rename process.
Fig 8
Figure 9 shows the second part of the rename process.
Fig 9
Now let’s contrast all of this with an event that is part of the good old standard auditing. Let’s take moving an OU; with the Advanced Auditing we get id 5139 (fig 7), nice and easy to read and understand. Now here is id 4662 that you would get for the same thing with standard auditing, fig 10.
Fig 10
With standard auditing some of the other items that we looked at would be next to impossible with auditing, such as tracking when an OU is renamed and as you can see from fig 10 hard to read and understand if you did get an event.
Now if your AD is in Mixed Mode (W2k8 and W2k3) you are stuck with standard auditing.
Recommended Windows 2008 Audit Policy
Randy F. Smith has a good resource for the Windows 2008 Audit Policy.
Windows 2008 Local Connections only
We had a Windows 2008 server in one of our labs that was setup by someone else and it was not allowing connections to the Internet. But we could remote to it and connect to it’s shares. Upon checking here is what I found:
1. Under Network Connections the connectivity showed Local only
2. Properties for the NIC were configured correctly
3. Running ipconfig from a command prompt shows the default gateway was 0.0.0.0
My steps to fix:
1. Open a command prompt with Admin rights
2. route delete 0.0.0.0
3. open the properties for your NIC and enter the correct defaut gateway.
That’s was all it took to give the system access to the Internet.
-
Archives
- February 2019 (1)
- October 2013 (1)
- August 2012 (1)
- December 2011 (1)
- May 2011 (1)
- July 2010 (1)
- March 2010 (1)
- February 2010 (1)
- December 2009 (1)
- November 2009 (1)
- October 2009 (1)
- September 2009 (1)
-
Categories
-
RSS
Entries RSS
Comments RSS